5 things in IT security Leading Companies got right in 2019
PLUS
5 things you need to know about IT Security in 2020 and
5 easy things you can get your team doing right now to stay secure!
Earlier in 2019, Maxsum security partner Sophos uncovered some very disturbing results in its independent survey of 3,100 IT managers.
Firstly that 70% of organisations had fallen victim to a cyber incident in the previous year that they were unable to prevent, and secondly, and even more alarmingly that 9 in 10 of these businesses said they actually had up-to-date security protections running at the time!
When you first see stats like these you’d be forgiven for taking the low road, and throwing your hands up in the air, like you just don’t care (even though we know you really do 😉) Don’t worry, you’ve just experienced a classic symptom of “cybersecurity fatigue”.
In the face of the constant onslaught of cyber incidents, it’s all too easy to just let what will be…well be. That is, until you get compromised and have to either report your breach or start notifying your clients! At that point, when you start going down the could’ve, should’ve, would’ve path, it’ll come as no surprise that it’s a whole lot harder to get back on track when you’re already behind the eight ball. And while you’re busy getting back up to speed, the bad guys are moving ahead and out-innovating you even faster and further.
But as with every challenge that seems overwhelming, breaking it down into smaller pieces is often the best way to forge a path forward.
So, we’ve done just that! We’ve wrapped up the top 5 things we’ve seen leading businesses do WELL in 2019 in the security stakes, and what’s changed over the course of 2019 that will inform the IT security choices proactive businesses will be taking from 2020 onwards!
5 IT Security Success Stories from 2019
Here are the top 5 things we’ve seen leading businesses on the road to cyber maturity starting to do well over 2019.
- MFA and Password “Hygiene”: Most cyber aware businesses by now have multifactor authentication enabled and are more proactive with regularly resetting secure passwords in line with password policies and using password management tools to layer up on password security.
- MDM: Many businesses will have sought to mitigate the threats posed by unmanaged or lost mobile devices by implementing Mobile Device Management.
- Security governance reviews: Many businesses are now proactively looking for and trialing ways to assess and measure their organisation’s security stance in some form on a regular basis, including dark web monitoring.
- Security awareness training: Leading businesses by now have made security best practices a regular talking point across the organisation to help mitigate those front-line, human error-based risk factors! Next step? Automating the process!
- Data breach response execution: Those organisations that experienced a data breach and implemented recommended mitigation strategies successfully prevented a secondary breach of the same nature in nearly 100% of cases (as opposed to organisations that failed to implement post-breach recommendations and suffered repeat incidents (up to another 4 times in one case!)
These are all great strides forward for businesses ahead of the curve! Congratulations if you’re ticking all 5 of these off your to-done list for the year!
But what many businesses still may not realise is that all of these measures are baseline level requirements in today’s cyber landscape. Think of them if you will as the new “costs of entry” into business; the minimum viable provisions you need to have in place to operate securely in today’s business landscape.
With this in mind, let’s look at what’s changed over 2019, so that you can keep the momentum going and build on how far you’ve come by making informed choices about your IT security options in 2020.
5 New IT Security Realities Exposed in 2019
Here’s a short list of the top five developments in the IT security landscape we’ve seen on the front lines in 2019, with reference also to the broader statistical findings presented by Sophos.
1. Modern cyber-attacks are automated and coming from multiple directions.
Not too long ago when it came to IT security, we viewed businesses like cities that we surrounded by erecting impenetrable walls so that, as long as the drawbridge was drawn and guarded, you could assume you were safe!
But today’s businesses are not like the medieval cities of the past. They are modern urban ecosystems, accessible and connected via an ever-changing network of interconnected tunnels, roads, highways, railways, bike tracks, and air routes (UberAIR anyone?) Just like our cities of 2020, your business has a multitude of non-static access points and moving targets, each of which is vulnerable to a range of security threats.
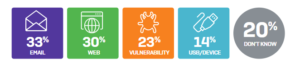
To complicate matters, one area where malicious actors are already out-innovating us is in their use of advanced automation and machine learning tools to auto-generate, deploy, manage and adapt their attacks remotely and at scale.
To meet fire with fire then, our IT security strategies need to be more comprehensive than ever before. They need to look at all the processes and technologies we have in place across all our “access points” to detect, contain, remediate, respond, prevent and review cyber incidents. PLUS, we need to get serious about levelling up to next-generation synchronised security products that leverage machine-learning-based automated threat detention and response mechanisms.
2. New-gen cyberattacks today are multi-stage, coordinated and blended.
A classic example of this has been the spate of Dropbox and Office 365-based phishing attacks experienced over 2019.
In short, you receive an email with a link to a document. You click on the link and enter your Dropbox and Office 365 credentials to access or download said “document”. No harm done at that point it would seem, but what has actually happened is that by entering your credentials into a fake Dropbox or Office 365 site, you given up your credentials to malicious actors who harvested them to use or onsell, accessed your data and/contacts to launch further phishing attacks, or perhaps gained access to you systems to capture sensitive data, or launch more harmful ransomware or server attacks.
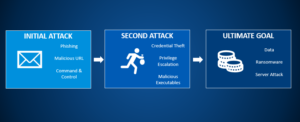
We’ve seen some stunning attacks this year, where malicious actors have used compromised DropBox credentials to actually sign up for and pay for premium DropBox account subscriptions (using stolen credit card details) to leverage for bigger next-stage attacks!
3. Businesses are lacking the technology, talent, time and budget to deal with evolving and emerging cyber threats
The same SOPHOS survey mentioned above found that up to 26% of an IT teams time is spent managing IT security. That’s a resource cost to your business of more than a week a month playing whack-a-mole, instead of staying ahead of the curve.
Just think about this statistic for a moment, next time someone asks you about cybersecurity and you default to your standard “Oh, our IT handles all of that…” Do they? Can they?
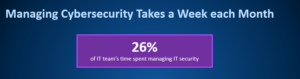
Might be time to look at what technology, talent, time and budget your IT team actually needs to take your IT security stance to the next level.
4. We’re only human after all!
One of the most compelling insights we’ve gained from tracking Australian data breach reporting statistics since the launch of the Notifiable Data Breaches Scheme in 2018, has been that the percentage of reported data breaches attributable to human error continues to remain at around 35% quarter to quarter.
Why is human error still such a key issue despite an increased effort to communicate and share the risks to and within businesses? Shouldn’t that percentage be dropping over time if more people are talking about IT security more often?
We see 3 reasons why the human factor is still a major issue:
- The top-down and front-line messaging just isn’t consistent enough within businesses, leading to security vigilance simply falling off employee’s radars.
- Malicious actors are continuing to find new and inventive ways to capitalise on our human vulnerabilities. Even more of a reason to keep the information and awareness push going strong across your teams.
- People’s working days are just so busy, and their turn-around times are so tight that security best practices are sometimes sacrificed in the need for speed! This is why regular security reviews of not just your systems, but your business processes as well are essential, as well as moving to next-generation security products that leverage predictive and automated threat detection, management and mitigation is essential.
5. We’re still being Phished hook, line and sinker, and BECs are the bait!
Every day we are seeing more convincing examples of phishing emails doing the rounds, and they are becoming more specific and tailored to individual users.
If fact, once an employee clicks on a more generic phishing email, it’s often the case that instead of simply mass harvesting contacts and data for onsell, the attacker is actually using the employee’s credentials to set up a Business Email Compromise sting by using the harvested data to impersonate a known and trusted contact for financial gain.
Based on incidence and cost to business, Business email compromise has been ranked as the fastest growing online scam in Australia right now.
If you’re not talking about the connection between phishing and business email compromises to your team already, get started now!
5 IT Security Agenda Items for 2020
So, to get you off on the right foot, here are our top 5 security questions to raise at your next management meeting to keep you on track to cyber maturity!
- Have you got the “cost of entry” items sorted? Have you implemented the ASD’s Essential Eight recommendations?
- Do you know how recently IT/Management has reviewed your approach to security?
- Does IT regularly report on cybersecurity incidents, resolutions, and future approaches to management?
- Have you recently allocated any additional resources to IT security, given the huge surge in the number of incidents out there, the complexity of those attacks and the knowledge required to get ahead of emerging threats?
- Is IT security, both from a technical and business process perspective, regularly raised with employees and at meetings?
5 Things You Can Get Your Team Doing to Stay Secure!
To get you started, here’s our latest Maxsum Play video blog on 5 things you can get your team doing to boost your security stance on the front line right now. Why not check raise them at your next meeting?

Ready to talk IT Security in 2020 and beyond? Get in touch with Maxsum today to find out more about our MaxSec suite of IT security offerings.
The Impossible Puzzle of Cybersecurity – A Whitepaper by Sophos and Maxsum Consulting on the emerging cybersecurity challenges faced by 3,100 IT managers globally.



